Security and Fine Grained Access Control
As a build and release management server, QuickBuild protects build information from unauthorized access at its best. Data traffic can be encrypted with SSL, and permission check is applied when accessing QuickBuild either through web interface or through remote API. The access control granularity is fine enough and almost all non-administrative functionalities can be access controlled. For example, you may authorize your customers to download artifacts of your release configuration, but prevent them from accessing your build log and unit test results, etc. Besides the ability to maintain its own user database, QuickBuild can also be configured to delegate user and group management functionality to your existing LDAP and Active Directory servers.
Protect QuickBuild with SSL and IP address binding
SSL can be enabled with minimum configuration, to protect traffic from browser to QuickBuild server, or between QuickBuild server and QuickBuild agents. Further, both QuickBuild server and agent can be configured to bind to specific ip address to consolidate security of the system.
Role based security and per-project access control
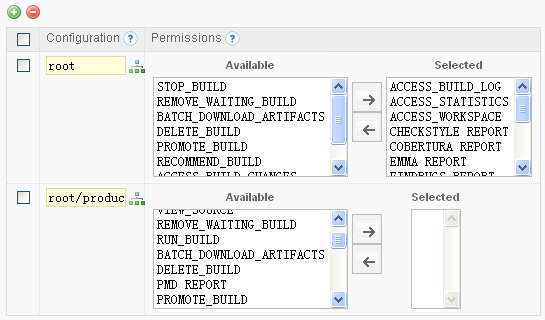
QuickBuild's permission control is role based. The administrator creates different roles in the system with appropriate permissions to selected configurations, and users belong to that role will have the same permission automatically. For example, you may create tester and release engineer roles, so that testers can access and recommend builds, while release engineers can access and promote recommended builds as release builds. To facilitate the task of permission assigning, one can define permission sets to assign same set of permissions to different configurations easily.
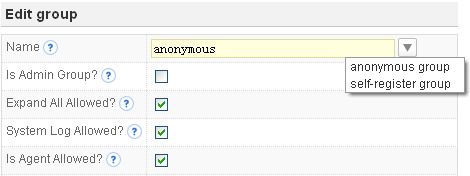
Optional anonymous access and user self-registering
Anonymous access can be enabled just by creating a special anonymous group with appropriate permissions. You can also make your users being able to register their account by themselves and all self-registered account will automatically have the permissions you specified for the register group.
LDAP and Active Directory integration
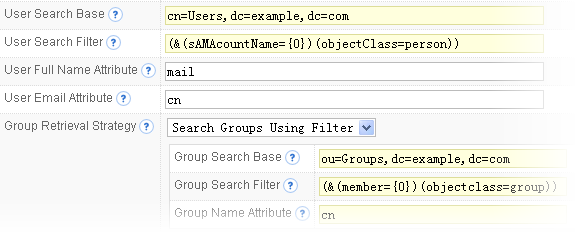
QuickBuild's integration with LDAP and Active Directory server is very flexible. Multiple LDAP and Active Directory servers can be configured, and QuickBuild will authenticate user through them one by one, until a successful authentication is done. If none of these servers authenticate the user successfully, QuickBuild will resort to authenticate the user using its own database. For externally authenticated users, you can instruct QuickBuild to respect associated group information maintained in external system, or to ignore the external groups, and use the group information maintained inside QuickBuild.
Single sign-on integration
QuickBuild can be configured to work in a single sign-on environment, with some third party software (such as Apache httpd server) actually authenticating the user and then forward the authenticated user name to QuickBuild via a http header by means of reverse proxy. As long as your single sign-on solution works with popular web server such as Apache httpd, it will work with QuickBuild via this approach.

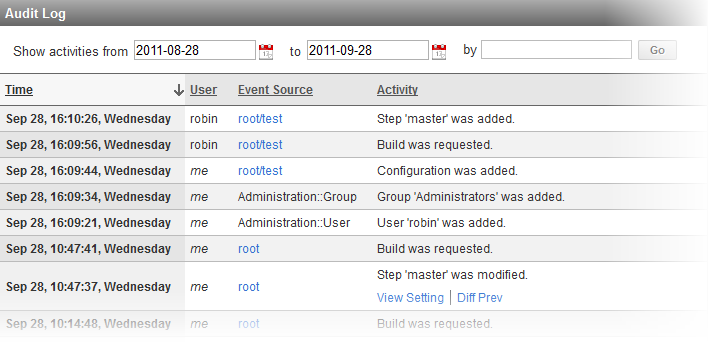
Audit of User Activities
QuickBuild audits all user activities in the system such as configuration modification, build triggering/cancelling. Authorized users may open the audit log to find out what has been changed in the system during a certain time period, and can compare the changes if necessary.